2019-01-25
[public] 52.6K views, 2.07K likes, 13.0 dislikes audio only
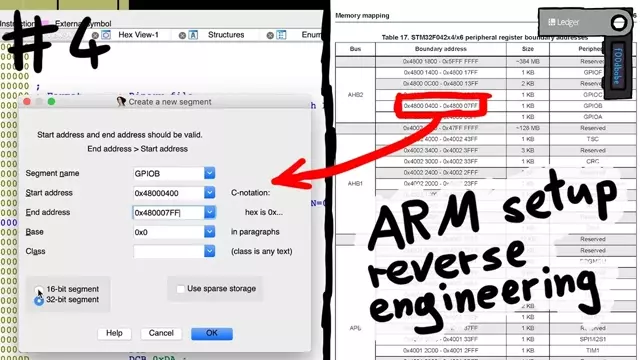
We are using IDA to setup segments for the ARM hardware and then find the entry-point through static and dynamic analysis.
research: https://wallet.fail
DISCLAIMER: The security research shown here was done a while ago and since then the software and hardware was updated; These videos are not sponsored or endorsed by Ledger.
-=[ 💻 Related Products ]=-
→ Ledger Nano S:* https://amzn.to/2VAhMvM
→ USB Hub with switches:* https://amzn.to/2SJuaYv
→ any STM32 Nucleo-64 development board:* https://amzn.to/2VDDE9J
-=[ 🔴 Stuff I use ]=-
→ Microphone:* https://geni.us/ntg3b
→ Graphics tablet:* https://geni.us/wacom-intuos
→ Camera#1 for streaming:* https://geni.us/sony-camera
→ Lens for streaming:* https://geni.us/sony-lense
→ Connect Camera#1 to PC:* https://geni.us/cam-link
→ Keyboard:* https://geni.us/mech-keyboard
→ Old Microphone:* https://geni.us/mic-at2020usb
US Store Front:* https://www.amazon.com/shop/liveoverflow
-=[ ❤️ Support ]=-
→ per Video: https://www.patreon.com/join/liveoverflow
→ per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join
-=[ 🐕 Social ]=-
→ Twitter: https://twitter.com/LiveOverflow/
→ Website: https://liveoverflow.com/
→ Subreddit: https://www.reddit.com/r/LiveOverflow/
→ Facebook: https://www.facebook.com/LiveOverflow/
-=[ 📄 P.S. ]=-
All links with "*" are affiliate links.
LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
#ReverseEngineering #HardwareSecurity
/youtube/video/EpA25bCHHtk
/youtube/channel/UClcE-kVhqyiHCcjYwcpfj9w
/youtube/video/9CS3q0uG1LI
https://www.patreon.com/join/liveoverflow
/youtube/video/nNBktKw9Is4