2017-07-07
[public] 77.8K views, 2.07K likes, 10.0 dislikes audio only
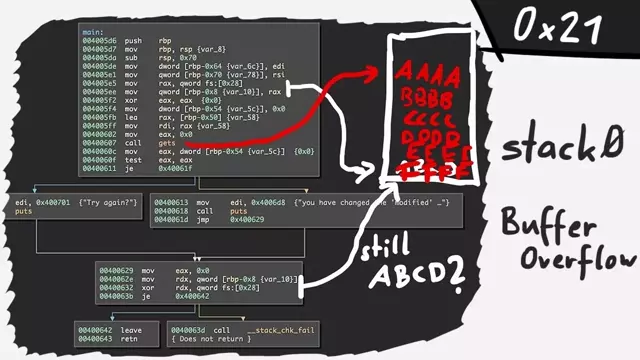
We have a look at stack level 0 from exploit-exercises.com/Protostar and compile it on a current Ubuntu, to see if it's still exploitable.
stack0: https://liveoverflow.com/binary_hacking/protostar/stack0.html
digitalocean referral:* https://m.do.co/c/826f195e2288
-=[ ❤️ Support ]=-
→ per Video: https://www.patreon.com/join/liveoverflow
→ per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join
-=[ 🐕 Social ]=-
→ Twitter: https://twitter.com/LiveOverflow/
→ Website: https://liveoverflow.com/
→ Subreddit: https://www.reddit.com/r/LiveOverflow/
→ Facebook: https://www.facebook.com/LiveOverflow/
-=[ 📄 P.S. ]=-
All links with "*" are affiliate links.
LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
#BinaryExploitation #BufferOverflow
/youtube/video/T03idxny9jE
/youtube/video/4HxUmbOcN6Y?t=39.889999
/youtube/video/4HxUmbOcN6Y?t=132.23
/youtube/video/4HxUmbOcN6Y?t=630.67999
/youtube/channel/UClcE-kVhqyiHCcjYwcpfj9w
/youtube/video/9CS3q0uG1LI
/youtube/video/iyAyN3GFM7A
https://www.patreon.com/join/liveoverflow