2023-05-31
[public] 71.0K views, 7.15K likes, dislikes audio only
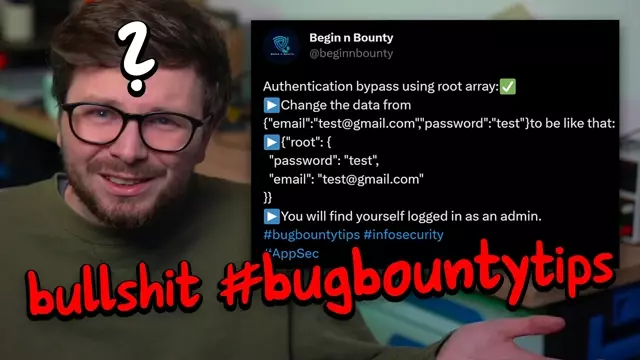
Lots of #bugbountytips get posted on twitter, but some of them are ... weird. Let's explore the technical details of one tweet to understand where this tip came from, why this tip was wrong, and eventually learn about the real underlaying vulnerability. This is a surprising turn of events!
advertisement:
Get my handwritten font https://shop.liveoverflow.com
Checkout our courses on https://hextree.io
Authentication Bypass Due to Empty Where Clause and SQL Injection in CodeIgniter https://liveoverflow.com/authentication-bypassing-in-codeigniter-due-to-empty-where-clause/
Thank you Eslam for sharing the details with us!
Follow Eslam on Twitter: https://twitter.com/eslam3kll
The #bugbountytips tweet: https://twitter.com/beginnbounty/status/1526795822687346688
Eslam's old post: https://infosecwriteups.com/authentication-bypass-using-root-array-4a179242b9f7
Eslam's new blog: https://eslam3kl.gitbook.io/blog/bug-hunting-findings/authentication-bypass-using-empty-parameters.
Day[0] Podcast: https://dayzerosec.com/vulns/2022/03/28/an-odd-authentication-bypass.html
Chapters:
00:00 - Intro
00:41 - The bugbountytips Tweet
01:21 - The Original Blog
02:43 - Talking to Eslam about the Happy Accident
04:36 - Digging Deeper
05:39 - Researching Login Code with Codeigniter
06:54 - Example Vulnerable Login Code
08:08 - Improving the Writeup
09:18 - Surprise SQL Injection!
11:37 - Conclusion
12:31 - hextree
=[ ❤️ Support ]=
→ per Video: https://www.patreon.com/join/liveoverflow
→ per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join
2nd Channel: https://www.youtube.com/LiveUnderflow
=[ 🐕 Social ]=
→ Twitter: https://twitter.com/LiveOverflow/
→ Streaming: https://twitch.tvLiveOverflow/
→ TikTok: https://www.tiktok.com/@liveoverflow_
→ Instagram: https://instagram.com/LiveOverflow/
→ Blog: https://liveoverflow.com/
→ Subreddit: https://www.reddit.com/r/LiveOverflow/
→ Facebook: https://www.facebook.com/LiveOverflow/
/youtube/video/2vAr9K5chII?t=41
/youtube/video/2vAr9K5chII?t=81
/youtube/video/2vAr9K5chII?t=163
/youtube/video/2vAr9K5chII?t=276
/youtube/video/2vAr9K5chII?t=339
/youtube/video/2vAr9K5chII?t=414
/youtube/video/2vAr9K5chII?t=488
/youtube/video/2vAr9K5chII?t=558
/youtube/video/2vAr9K5chII?t=697
/youtube/video/2vAr9K5chII?t=751
/youtube/video/nDiXoeeAMWM
https://liveoverflow.com/support
/youtube/video/LrLJuyAdoAg